Crucial Role of IT Management in Cybersecurity

Cybersecurity is a critical problem for businesses and communities of all sizes. From the smallest start-ups to multinational corporations, the need for robust, adaptive, and forward-thinking cybersecurity measures is paramount. Today we’re exploring the multifaceted role of IT management in establishing, enforcing, and evolving cybersecurity strategies, highlighting its importance in a world where cyber threats are an ever-present reality.

Strategic Planning and Cybersecurity
The role of managed IT services extends beyond day-to-day operations and crisis management. It is instrumental in strategic planning as well. Cyber threats are evolving, and new vulnerabilities can be exposed at any moment. It must keep abreast of these developments and plan for them. This could suggest investing in new security software or hardware or implementing new policies and procedures to enhance security.
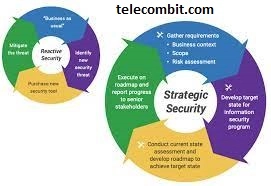
Policy Development and Enforcement
Policies guide the behavior and decisions within an organization. In the realm of cybersecurity, this is no different. Managed IT is responsible for developing, implementing, and enforcing specific and well-developed cybersecurity policies, ranging from password creation guidelines to rules about using personal devices at work. The goal of these policies is to reduce the risk of a cybersecurity incident and ensure that, if an incident does occur, the impact is minimized and the response is swift.
You can also learn about: Thriving Event Planning and Management

Monitoring and Responding to Cyber Threats
Another key aspect of these managed services in cybersecurity is monitoring for and responding to cyber threats. This involves using various tools and technologies to determine possible hazards and respond to them before they generate substantial harm. This job can be difficult due to the ever-evolving character of cyber hazards, but it is necessary to keep the security of an organization’s IT help.

Integration of IT and Business Strategy
It is increasingly clear that IT strategy and business process can no extent, be siloed, particularly where cybersecurity is discussed. It is responsible for assuring that all systems, including cybersecurity, align with and help the wider company plan. This could affect operating near other company units to confirm that cybersecurity efforts improve rather than impede business processes.
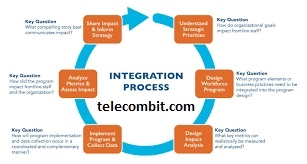
Financing in Cybersecurity Resources
IT management via organizations such as Virteva helps a company make judgments about aid distribution. This power has judgments about the funding for cybersecurity software and hardware, the hiring of personnel, or the percentage of time and budgets to cybersecurity activity and understanding timetables. In creating these findings, technological leadership must offset the need for strong cybersecurity efforts with other industry needs and conditions.

Worker Training and Awareness
In numerous cybersecurity happenings, human mistake plays an important part. IT handling can mitigate these risks by running periodic training and understanding schedules. These enterprises should protect safe internet usage, password protection, identifying phishing scams, and the best methods for data security. Continuous activity not only provides workers with the ability to act securely but also allows instill a healthy security-first philosophy.

Conclusion
In an era where cyber hazards are a regular concern, the role of IT management in cybersecurity cannot be overstated. From formulating robust strategies to fostering a culture of awareness and embracing cutting-edge technologies, IT management is the guardian of an organization’s digital assets. By recognizing the multifaceted responsibilities of IT management in cybersecurity, organizations can establish a strong line of defense against the ever-evolving landscape of cyber threats.





